When the health insurance giant Anthem announced it was the victim of a hack that may have exposed the data of up to 80 million customers last week, Mark McLarnon had an idea of what was happening behind the scenes.
“I’ve been in the shoes of the folks that are affected by this before,” the cybersecurity expert said. “It hits close to home.”
Now the CTO of Inner Harbor-based CyberPoint International, McLarnon has worked in network defense and computer forensics for the government and private sector for 15 years. He’s one of the many Baltimore-area cybersecurity workers who’s been on the other side of the breach as an investigator.
While it’s his job to investigate and provide protection against such incidents, McLarnon said he takes no joy out of seeing a major attack.
“I never like to hear about any breaches,” he said.
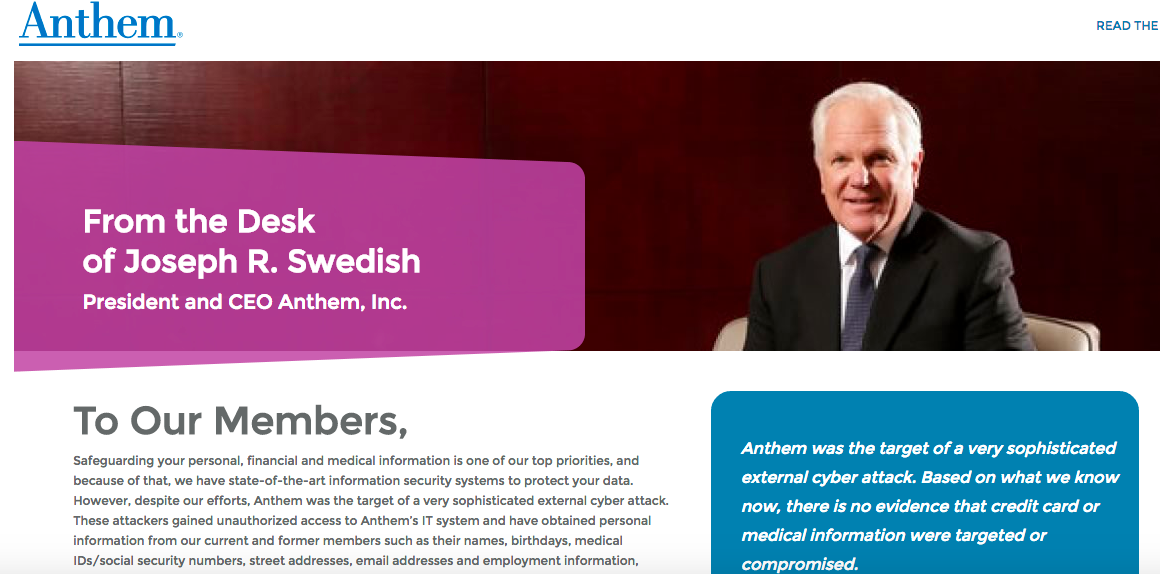
The Anthem breach was reported Wednesday night. According to a message posted online, the hackers gained access to customers’ personal information including names, birthdays, Social Security numbers and income data. The company, which offers BlueCross Blue Shield plans in California, New York and other states, is still working to determine the extent of the breach, but medical data isn’t believed to have been compromised.
The breach comes on the heels of high-profile breaches at Sony, Home Depot and Target. McLarnon points out that the FBI issued a warning to the healthcare industry on two occasions in 2014. One message, issued in August, noted “malicious actors targeting healthcare related systems.”
Anthem, and the healthcare industry in general, is a target because of the Social Security numbers that were likely accessed, said Gavin Millard. The technical director at Columbia-based Tenable Network Security said stolen credit card data doesn’t fetch what it used to on the black market.
“It’s really, ‘How much money can these attackers make from breaking in?'” he said. “Forty to 60 million Social Security numbers is probably worth quite a bit of money on the black market.”
CyberPoint’s McLarnon gave the company credit for reporting the hack within a week and making services like free credit monitoring and fraud alert monitoring services available.
“Anthem has taken very definitive steps,” he said.
Millard said the speed of those steps was an anomaly.
Sometimes, most of the public doesn’t even hear about breaches. In this case, the message posted online came directly from the company’s CEO, Joseph Swedish.
“That kind of post-breach PR outreach is a really important factor that lots of organizations forget about and don’t do a really good job of,” Millard said, adding that a strong message can help reassure customers that the company can handle the incident.
Perhaps not surprisingly, not all of the public relations necessarily paints the full picture. The cause of the Anthem breach has yet to be determined, but Swedish’s message did say that the attack was “very sophisticated.” That’s typical, said Millard, but not necessarily accurate.
“In reality, the attackers often use simple methodologies to break in,” Millard said, such as phishing schemes via company email, or exploiting employees who didn’t update antivirus software.
Anthem is already coming under fire because it didn’t encrypt the Social Security numbers. According to the Wall Street Journal, companies aren’t required to encrypt the data. McLarnon advocates using the practice “whenever possible.”
On the other hand, Millard points out, using encryption doesn’t make a company completely protected from an attack.
“Although encryption is a very good control, it doesn’t always mean that the data is totally secure,” Millard said. The Tenable exec points out that it is used as a “last bastion” of security when people have done other things that leave them vulnerable.
Both experts advocate preventative action. Tenable offers a vulnerability scanner that assesses company systems. At CyberPoint, McLarnon advocates training customers in how to look for warning signs of an attack. If data may have been stolen, McLarnon also said it’s important to check lines of credit, taxes and other potential points where their data could’ve been used fraudulently. While it may not show up immediately, the stolen information can have a “cascading effect” on people for years.
“Although it may seem vague, vigilance is always urged,” McLarnon said.
Before you go...
Please consider supporting Technical.ly to keep our independent journalism strong. Unlike most business-focused media outlets, we don’t have a paywall. Instead, we count on your personal and organizational support.
3 ways to support our work:- Contribute to the Journalism Fund. Charitable giving ensures our information remains free and accessible for residents to discover workforce programs and entrepreneurship pathways. This includes philanthropic grants and individual tax-deductible donations from readers like you.
- Use our Preferred Partners. Our directory of vetted providers offers high-quality recommendations for services our readers need, and each referral supports our journalism.
- Use our services. If you need entrepreneurs and tech leaders to buy your services, are seeking technologists to hire or want more professionals to know about your ecosystem, Technical.ly has the biggest and most engaged audience in the mid-Atlantic. We help companies tell their stories and answer big questions to meet and serve our community.
Join our growing Slack community
Join 5,000 tech professionals and entrepreneurs in our community Slack today!

The man charged in the UnitedHealthcare CEO shooting had a ton of tech connections

From rejection to innovation: How I built a tool to beat AI hiring algorithms at their own game

Where are the country’s most vibrant tech and startup communities?