Browsers are our window into the virtual world.
So often though, we forget that just as we are looking outward, companies are looking inward. Every search we perform is logged and tied to our virtual footprint (and amongst other things, our geographic location). Search surveillance consequences span from differential pricing (like a higher online price if your browser denotes your location as affluent) to the inability for people to access sensitive information in countries with strict censorship laws (countries, for example, restricting access to sites about AIDS). Access to the amount and kinds of information internet architecture provides is unprecedented, and we are only beginning to understand the implications.
This is where The Onion Router (Tor) comes in. The Tor browser obscures any personal ties and information (with a few exceptions) associated with your browsing history. When you use Tor, instead of your request going straight from your browser to the site (like from my DuckDuckGo search right to technical.ly/philly), it reroutes through several different countries. When using Tor, my request then might go through Norway and Germany before reaching technical.ly/philly. You might imagine that when using Tor, you are not only putting shades on your window but also removing your house from the map or Streetview entirely.
The overall strategy of Tor is that the more people who use it, the stronger of a tool it is. For activist and West Philly-based Tor Communications Director Katie Krauss, using Tor is not just switching a browser.
“Using the Tor browser is a civic act — it allows you to protect your right to privacy, and at the same time it helps human rights activists in countries like Iran or China to use the Internet without getting a knock on the door,” she said.
The Tor Project also has Philly roots, as cofounder and research director Roger Dingledine used to be a visiting professor at Drexel.
Below are screenshots and some narrative about my experience downloading and using Tor.
1. To download the Tor browser, I went to the Tor project’s download page and selected the Mac option.
(Screenshot)
2. Once the browser bundle downloaded, I dragged the Tor icon to my Applications folder.

(Screenshot)
3. After clicking the Tor icon, the Tor network settings options asked me to select an option in order to connect. I selected the first option “connect,” which is recommended to attempt first by Tor documentation.
(Screenshot)
4. Shortly afterwards, I was connecting to the Tor network.
(Screenshot)
5. Within minutes, I was connected.
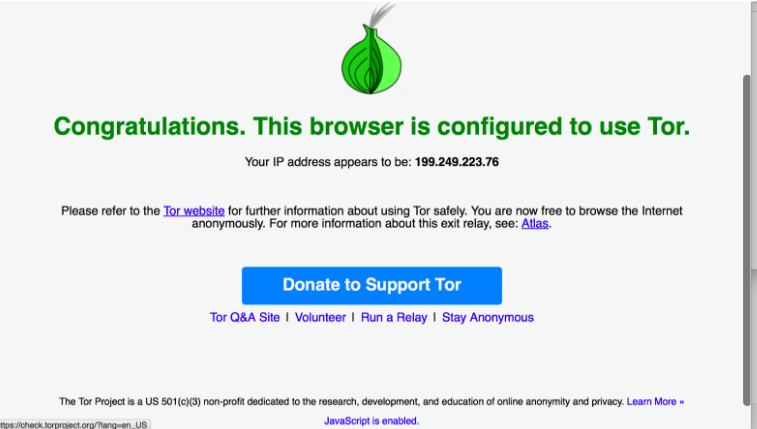
(Screenshot)
6. I tested out the browser by going to cnn.com. Under the Tor onion icon, I was able to pull up the Tor circuit, or what countries were bounced through on my way to the site. You can see here how other addresses create a layered, onion-like effect around my initial request.
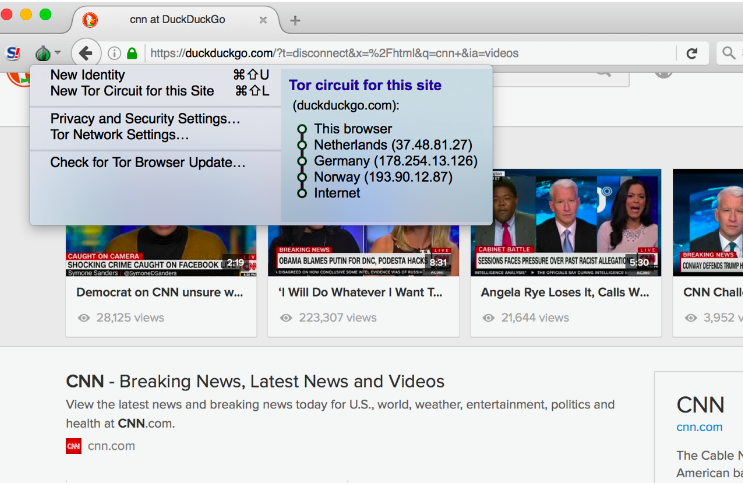
(Screenshot)
7. However, when I tried to login to Facebook, I was locked out.
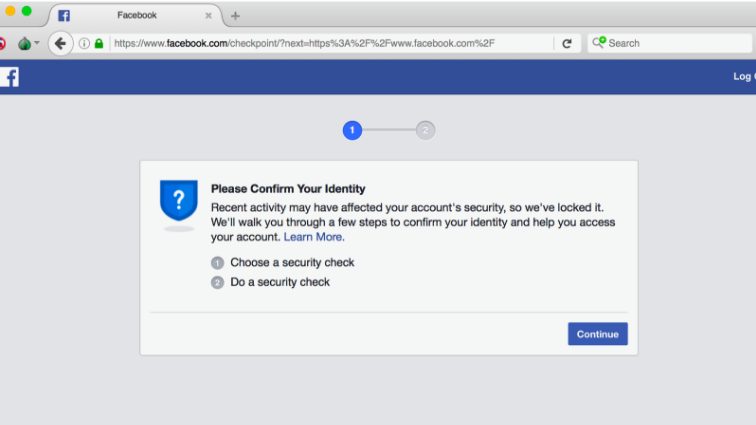
(Screenshot)
8. The same thing happened when I attempted to login to Gmail.

(Screenshot)
When logging on to Facebook and Gmail, Tor wouldn’t have masked my identity (instead it would prevent certain kinds of advertising and tracking). However, both Facebook and Gmail gave me error messages.
9. I restarted the Tor browser with a fresh identity.
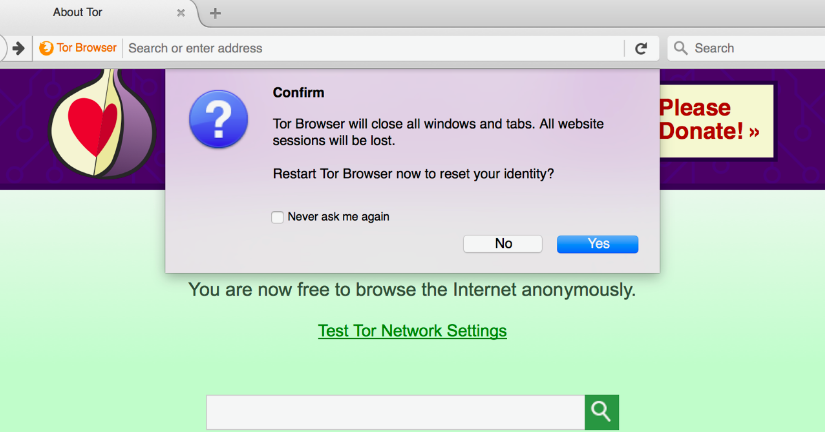
(Screenshot)
Unfortunately, this was to no avail. Facebook was alerting me that my account was likely compromised, because my last shown login was from Colombia. After attempting verification steps, I was locked out of both of my accounts.
I contacted Krauss to see if this was typical or Tor-related. She gave me the Facebook loophole: “The way to avoid this with Facebook is to use their onion address (put this into the address bar on the Tor browser and it will take you to Facebook): https://facebookcorewwwi.onion/.” For more info, she directed me to this Facebook blog post.
Krauss noted that she and several other users she checked with have no problem with Gmail in the Tor browser, though it is possible that the issue was the Tor-Gmail interface.
In the end, it worked for me: I was locked out of Gmail for about 3 hours, but after attempting again, I was able to sign in (though I had to verify with an extra step). While it was frustrating to be locked out of my email for a bit, the experience drove home for me how location dependent verification is (and the potential consequences of such dependence).
Overall, Tor was easy to implement and the inconvenience of switching browser was worth the benefit. I’ve since relapsed since I first used it because it’s faster to go log on in Chrome and I need Google Hangouts for work (I haven’t been able to use it on Tor) but I am back on Tor now.
As I was browsing and watching the latest news, the onion metaphor made me beyond the technical aspect of Tor: if we imagine that those whose civil rights are most vulnerable are in the center, we can effect change by layering around them — even with as simple an act of a browser change.
Before you go...
Please consider supporting Technical.ly to keep our independent journalism strong. Unlike most business-focused media outlets, we don’t have a paywall. Instead, we count on your personal and organizational support.
3 ways to support our work:- Contribute to the Journalism Fund. Charitable giving ensures our information remains free and accessible for residents to discover workforce programs and entrepreneurship pathways. This includes philanthropic grants and individual tax-deductible donations from readers like you.
- Use our Preferred Partners. Our directory of vetted providers offers high-quality recommendations for services our readers need, and each referral supports our journalism.
- Use our services. If you need entrepreneurs and tech leaders to buy your services, are seeking technologists to hire or want more professionals to know about your ecosystem, Technical.ly has the biggest and most engaged audience in the mid-Atlantic. We help companies tell their stories and answer big questions to meet and serve our community.
Join our growing Slack community
Join 5,000 tech professionals and entrepreneurs in our community Slack today!

The person charged in the UnitedHealthcare CEO shooting had a ton of tech connections

From rejection to innovation: How I built a tool to beat AI hiring algorithms at their own game

How a laid-off AI enthusiast pivoted to become a founder — while holding down a day job


