To Danny Rogers, the recent spate of high-profile hacks that have hit giant healthcare companies like Anthem and financial firms like JPMorgan Chase and even the U.S. government all share one characteristic: They could have been detected sooner.
Rogers and fellow Johns Hopkins Applied Physics Lab (APL) alum Michael Moore saw law enforcement and intrepid journalists (like the renowned cybersecurity reporter Brian Krebs) finding out about hacks before the companies themselves. And usually, Krebs and police (sometimes in that order) don’t come in until a few weeks later.
With Matchlight, a software platform that came out of stealth mode in June, Rogers, Moore and their startup Terbium Labs are looking to help companies cut the time it takes to find out their data was stolen.
Rogers acknowledges that this requires companies to abandon a certain assumption.
“You can no longer assume that you’re not going to get breached,” the former APL program manager said. “No matter what you throw at it, you have to understand that your data is still at risk.”
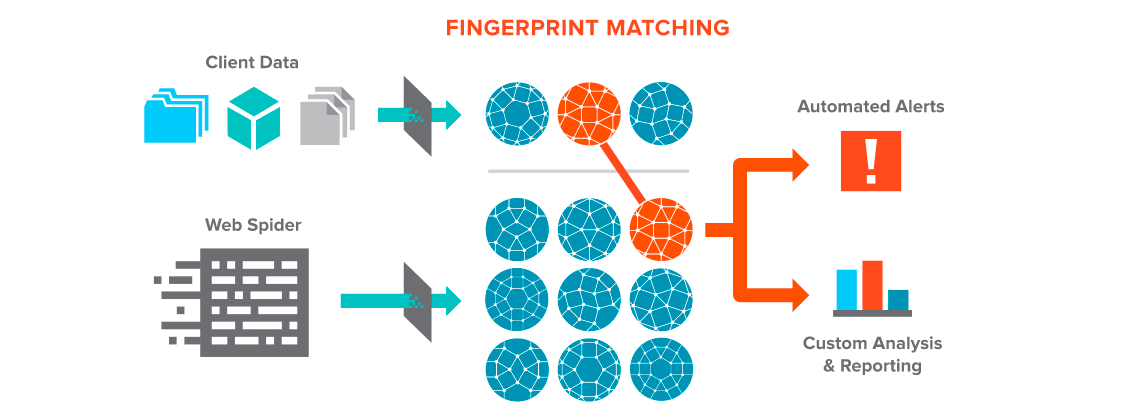
In place of the human trackers, the program sends out automated “crawlers” that scour the dark web and other digital spots where stolen data often ends up getting traded, Rogers said. A “data fingerprint” is attached to the potentially sensitive information. That’s used to keep tabs on the data, and means that the company doesn’t have to specifically know what’s in the stolen package to find it.
Matchlight can “search on behalf of clients without understanding what the data is,” Rogers said.
While the product is still fresh out of stealth mode, the company is looking to sign enterprise clients to use the program. He thinks it can be particularly effective in the financial and healthcare sectors, which have been targeted for big hacks recently. When he shows the product to potential clients, Rogers says he’s already hearing feedback that “no one else can do that at this point.” Investors have also shown interest, as the company recently raised more than $3.5 million, according to SEC filings.
The eight-person company is currently based out of offices in the Sharp-Leadenhall neighborhood of South Baltimore. Rogers expects the company to grow to 10 employees in the near future.
Asked about the decision to base the company in Baltimore, Rogers cited the strong cybersecurity talent pool in the area, as well as the relatively affordable real estate with proximity to New York and D.C.
“Baltimore is a great city to do this,” he said.
Join the conversation!
Find news, events, jobs and people who share your interests on Technical.ly's open community Slack

Baltimore daily roundup: Medtech made in Baltimore; Sen. Sanders visits Morgan State; Humane Ai review debate

Baltimore daily roundup: The city's new esports lab; a conference in Wilmington; GBC reports $4B of economic activity

Baltimore daily roundup: Find your next coworking space; sea turtle legislation; Dali raided and sued